Security is becoming more important for businesses operating in an increasingly complex landscape of cyber threats and data breaches. Small businesses often don’t have the advanced security measures and resources that larger enterprises possess, making them particularly vulnerable targets for cyberattacks.
A breach can result in significant financial losses, reputational damage, and legal liabilities, which can be catastrophic for small businesses. Therefore, investing in adequate security measures is essential, and in this post, we will look at the SAMM framework that allows us to take control of the situation.
What will we talk about?
- Understanding of what SAMM is and why people use it
- Reasoning for using it in your organization
- A suggestion on where to start
- There will be no practical implementation guide just yet
Is my business secure?
One day, you may find yourself wondering: how secure are we actually?
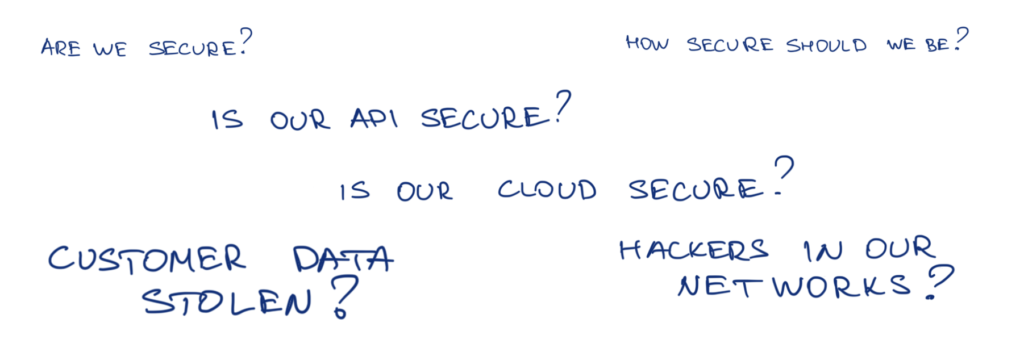
It’s easy to spiral down the thought thread and spend too much time thinking about these questions. The SAMM framework we’ll review will help you answer these questions faster and more reliably.
As a bonus, it will provide a clear structure for where your organization needs to improve and track the progress.
Why don’t I know the answer today?
Businesses face several challenges when assessing their security posture:
▶︎ Limited resources
Small and medium businesses (SMBs hereafter) often lack a security team to assess and manage their security posture.
Realistically, there will never be enough resources for cybersecurity. Businesses generate their revenue from the product increments they ship, and making that increment 20% or 80% more secure will not affect the revenue, at least not quickly enough to make the business happier.
▶︎ Complex (and ever-changing!) threat landscape
New cyber threats and attack vectors emerge regularly. SMBs with limited infosec resources will struggle to keep up with the developments, becoming vulnerable to attacks without even knowing that.
▶︎ Dependency on technology and 3rd party vendors
SMBs increasingly rely on technology for their day-to-day operations and may not fully understand the risks associated with their technology usage or how to secure their digital assets effectively.
Today, we have an easy-to-integrate-with SaaS available for everything we do: new employee onboarding, hotel booking for trips, IT support requests, employee training, and the list goes on.
▶︎ Lack of visibility
SMBs use cloud services or have distributed operations, and sometimes this infrastructure is set up without taking security into account because SMBs like to move fast, deliver, be on time and budget with projects, etc.
So what can we do to fix that?
Please welcome on stage: OWASP SAMM 🪩
OWASP SAMM (Software Assurance Maturity Model) is a comprehensive framework (read: covers all or most of your questions) designed to assist small businesses in evaluating their security posture effectively (read: with a small security team*).

Developed by the Open Web Application Security Project (OWASP), SAMM provides a structured approach for organizations to assess, improve, and benchmark their software security practices. SAMM was defined with flexibility in mind so that organizations using any style of development can customize and adopt it.
Using SAMM, small businesses can identify their current security maturity level, which enables them to:
- prioritize their security efforts
- allocate resources efficiently
- and establish a roadmap for enhancing their overall security posture in a cost-effective manner.
* the key word there is “evaluate”. You will not fix everything with, for example, a 3-people security team in a 5000 employees company, but this is outside of the scope of this discussion 😃
What SAMM covers
The SAMM framework outlines five key components (also called “business functions”)
for improving security posture:

Governance
Governance focuses on the processes and activities related to how an organization manages overall software development activities. This includes concerns that impact cross-functional groups involved in development, as well as business processes established at the organization level.
Design
Design concerns the processes and activities related to how an organization defines goals and creates software. This generally includes gathering requirements, defining high-level architecture specifications, and designing more detailed (technical) designs.
Implementation
Implementation is focused on the processes and activities related to how an organization builds, deploys, and manages software components and their related defects.
Activities within the Implementation function have the greatest impact on developers’ daily lives. The joint goal is to ship reliably working software with minimum defects.
Verification
Verification focuses on the processes and activities related to how an organization checks and tests artifacts produced throughout software development.
This typically includes quality assurance work such as testing but can also include other review and evaluation activities.
Operations
The Operations Business function encompasses those activities necessary to ensure confidentiality, integrity, and availability are maintained throughout the operational lifetime of an application and its associated data. Increased maturity with regard to this function provides greater assurance that the organization is resilient in the face of operational disruptions, and responsive to changes in the operational landscape.
Levels of Maturity
SAMM does not insist that all organizations achieve the maximum maturity level in every category. Each organization can determine the target maturity level that is the best fit and adapt the available templates for their specific needs.
SAMM is based on 15 security practices grouped into 5 business functions. Every security practice contains a set of activities structured into 3 maturity levels. The activities on a lower maturity level are typically easier to execute and require less formalization than the ones on a higher maturity level.
Why SAMM and not “framework X”? 🤔
Using OWASP SAMM for ongoing security improvement offers numerous benefits to small businesses.
- SAMM provides a structured approach to security assessment and improvement. It enables businesses to systematically identify and prioritize areas for enhancement based on their unique risk profiles and objectives.
- SAMM offers a clear roadmap for progression, allowing businesses to track their security maturity over time and measure the effectiveness of their security initiatives.
- SAMM promotes collaboration and communication among stakeholders by providing a common language and framework for discussing security-related issues and strategies.
One more benefit: SAMM is much easier to start with for a small/medium organization, and reaching maturity level 1 can already hit most of the security requirements 👈
Implementing SAMM for your business
It starts with a leadership buy-in. That, along with stakeholder involvement, is crucial for the successful implementation of security measures within a small/medium business. Without the support and commitment of leadership, security initiatives are likely to lack the necessary resources, prioritization,
and authority needed for effective implementation.
When leaders prioritize security, it sends a clear message throughout the organization that security is a top priority, fostering a culture of security awareness and accountability.
Sold! 👏 Where do I start?
To begin implementing SAMM, SMBs should start by conducting a comprehensive assessment of their current security posture and software development practices.
Assessment involves evaluating existing security policies, procedures, and controls across all aspects of the software development lifecycle. In new and ongoing projects, it will help surface potential customer requirements and expectations. After identifying strengths, weaknesses, and areas for improvement, SAMM will help prioritize the efforts to focus on the most critical areas first.
It’s worth mentioning again that gaining leadership buy-in and securing commitment from stakeholders is essential to getting the support and resources needed for SAMM implementation. Once the assessment is complete and priorities are established, businesses can then develop a tailored roadmap for gradually implementing SAMM practices.
An excellent place to start is the SAMM Toolbox, created by OWASP. You can use it to support an interview or workshop together with other people involved in your software development process. To learn more, please follow the link: https://owaspsamm.org/assessment/
In a separate blog post, we will use SAMMY, a management tool for the OWASP SAMM model, to implement SAMM in a fictional (though realistic) small business organization, so stay tuned for more! 🧑💻
What can go wrong
Several common challenges small businesses might face when implementing SAMM include the following.
⚠️ Resistance to change
Employees and stakeholders may resist changes to existing processes and workflows required to align with SAMM guidelines. Overcoming resistance to change and gaining buy-in for SAMM implementation can be challenging, especially in organizations with entrenched cultures or competing priorities.
Having a project with “burning” deadlines may be another huge obstacle.

⚠️ Resource constraints
We discussed resource limitations above, and they haven’t gone away since then! SMBs often have limited financial and human resources available for security initiatives. Implementing SAMM may require additional tools, training, and personnel investments, which can strain already tight budgets.
⚠️ Integration with existing processes
Integrating SAMM into existing development and security processes can be challenging, particularly if these processes are already established and ingrained within the organization. Ensuring seamless integration while avoiding disruption to ongoing operations needs careful planning and coordination.
These challenges can be made easier with proactive planning, stakeholder engagement, and a pragmatic approach to implementation.
Summing it up
The cyber landscape is getting more complex, making SMBs face unwanted yet significant challenges in maintaining robust security measures due to limited resources and expertise. The consequences of a breach can be devastating and likely to come unanticipated. To address these concerns, organizations can turn to frameworks like the OWASP SAMM, which are explicitly designed to evaluate and improve security practices, giving visibility and control in return.

SAMM offers a clear framework that facilitates collaboration, promotes security awareness, and allows businesses to track their progress over time. Implementing it may pose challenges such as resistance to change, resource constraints, and integration issues. Proactive planning, stakeholder engagement,
and a pragmatic approach can all help small businesses navigate these hurdles effectively.
All in all, it is well worth the returns, such as clear answers to the big questions from the “Is my business secure?” section above.
As mentioned earlier, in the next blog post, we will use SAMMY, a management tool for the SAMM model, to implement SAMM in a fictional small business organization, so stay tuned for more!
References
- About OWASP SAMM https://owaspsamm.org/about/
- About SAMMY: https://sammy.codific.com
- More on SAMM assessment: https://owaspsamm.org/assessment/
- SAMM Quick Start Guide: https://owaspsamm.org/guidance/quick-start-guide/



